Risk actors are utilizing superior malware to backdoor business-grade routers
[ad_1]

Researchers have uncovered superior malware that’s turning business-grade routers into attacker-controlled listening posts that may sniff e mail and steal information in an ongoing marketing campaign hitting North and South America and Europe.
In addition to passively capturing IMAP, SMTP, and POP e mail, the malware additionally backdoors routers with a distant entry Trojan that enables the attackers to obtain information and run instructions of their selection. The backdoor additionally permits attackers to funnel knowledge from different servers via the router, turning the machine right into a covert proxy for concealing the true origin of malicious exercise.
Black Lotus Labs
“This sort of agent demonstrates that anybody with a router who makes use of the Web can doubtlessly be a goal—and so they can be utilized as proxy for one more marketing campaign—even when the entity that owns the router doesn’t view themselves as an intelligence goal,” researchers from safety agency Lumen’s Black Lotus Labs wrote. “We suspect that menace actors are going to proceed to make the most of a number of compromised belongings along side each other to keep away from detection.”
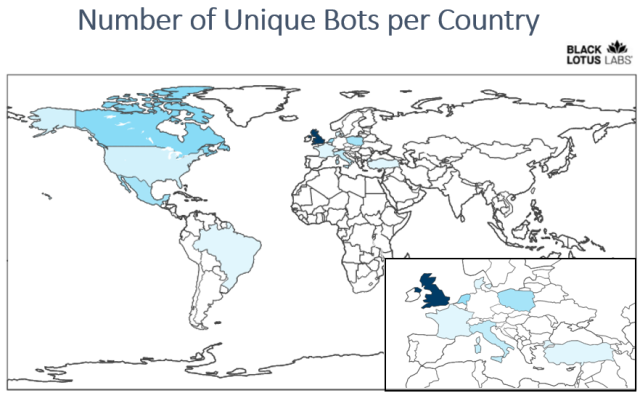
The researchers stated the marketing campaign, dubbed Hiatus, has been working since at the very least final July. Thus far, it has primarily hit end-of-life DrayTek Vigor fashions 2960 and 3900 working an i386 structure. These high-bandwidth routers assist digital non-public community connections for a whole lot of distant staff. To this point, roughly 100 routers have been contaminated, which is about 2 p.c of the DrayTek 2960 and 3900 routers uncovered to the Web. The researchers suspect the unknown menace actor behind Hiatus is intentionally retaining its footprint small to take care of the stealth of the operation.
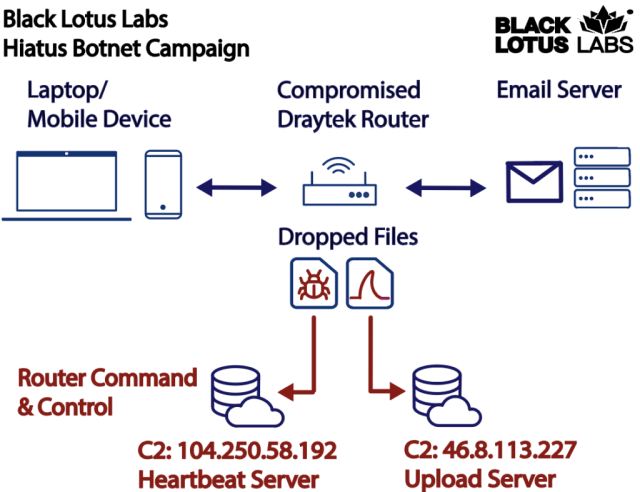
Black Lotus nonetheless doesn’t know the way units are getting hacked within the first place. As soon as and nonetheless that occurs, the malware will get put in via a bash script that’s deployed post-exploitation. It downloads and installs the 2 principal binaries.
The primary is HiatusRAT. As soon as put in, it permits a distant menace actor to do issues like run instructions or new software program on the machine The RAT additionally comes with two uncommon extra capabilities inbuilt: (1) “convert the compromised machine right into a covert proxy for the menace actor,” and (2) use an included packet-capture binary to “monitor router site visitors on ports related to e mail and file-transfer communications.”
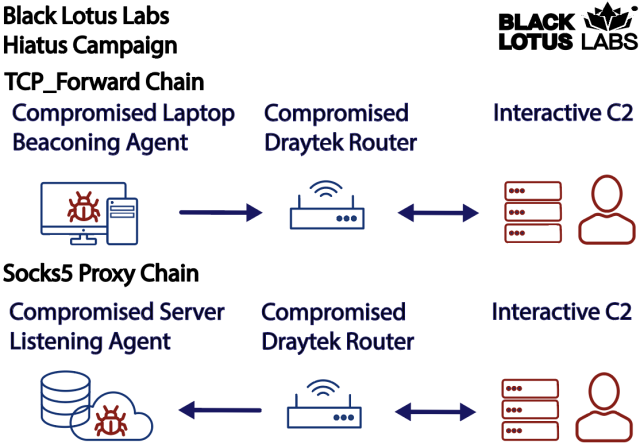
The researchers suspect the menace actor included a SOCKS 5 software program in operate 1 was to obfuscate the origin of malicious site visitors by proxying it via the contaminated router. Black Lotus researchers wrote:
The HiatusRAT tcp_forward operate permits a menace actor to relay their beaconing from a separate an infection via a compromised machine earlier than hitting an upstream C2 node. Conversely, they will additionally echo their command to an internet shell from upstream infrastructure via the compromised router within the nation of the focused machine, then work together with a extra passive agent to obscure their true origination supply by passing geo-fencing-based safety measures.
Black Lotus Labs
A tcpdump binary enabling packet seize was the engine behind operate 2. It gave Hiatus the power to observe site visitors on ports transmitting e mail and FTP communications from the adjoining LAN. It was preconfigured to work with the IMAP, POP, and SMTP e mail protocols.
Black Lotus Labs
Hiatus is especially concentrating on DrayTek routers working an i386 structure. The researchers, nonetheless, have uncovered prebuilt binaries compiled for ARM, MIPS64 massive endian, and MIPS32 little endian platforms.
The packet-capture means of the HiatusRAT ought to function a significant wake-up name for anybody nonetheless sending e mail that isn’t encrypted. In recent times, e mail providers have improved at mechanically configuring accounts to make use of protocols similar to SSL/TLS over port 993 or STARTTLS on port 143. Anybody nonetheless sending e mail in plaintext will seemingly remorse it sooner fairly than later.
It’s additionally a good suggestion to do not forget that routers are Web-connected computer systems, and as such, they require common consideration to make sure updates and different measures, similar to altering all default passwords, are adhered to. For companies, it might additionally make sense to make use of devoted router monitoring.
[ad_2]

No Comment! Be the first one.